MVP Award 2017-2018
SCUG.SE Client Days 2017 October 12-13 in Stockholm
SCUG.SE Welcomes you to two days of Client Management content at Microsoft in Akalla, Stockholm on the 12-13 of October! The Agenda is almost completed we have some slots that are not 100% decided yet, waiting response. We have some new speakers this time, it will be great! Almost all sessions are presented in Swedish!
On Thursday evening we are planning to meetup somewhere downtown Stockholm and continue the discussions.
Welcome!!
The agenda:
Day 1
Day 2
ConfigMgr Windows 10 Baseline, Laps, Applocker, Credential guard
I have written a couple of posts now on Configuration Items and Baselines in Configuration Manager so I thought it was time to collect them all here with a call for action! Create your own CI’s and Baseline to make sure that you don’t have any configuration drift out there. Many settings are configured using Group Policy and that is perfect but how many actually monitors the local event log on all computers to make sure they are applied?!
Yet we really on them for the configuration of our clients and security settings….
I have written some posts on how to monitor some features in Windows 10:
- The Local administrator account disabled – https://4sysops.com/archives/disable-the-local-administrator-account-with-sccm/
- Monitoring LAPS with Configuration Manager – https://4sysops.com/archives/monitoring-laps-with-configuration-manager/
- Configuration Manager CI to check that credential guard is running – http://ccmexec.com/2017/04/configmgr-ci-to-check-that-credential-guard-is-running/
- ConfigMgr CI to check Applocker is configured and running – http://ccmexec.com/2017/04/configmgr-ci-to-check-applocker-is-configured-and-running/
If we combine them we get a start at least, add your own settings that are important in your environment

There is a great script as well by Sam Roberts that can be used to export a Group Policy to a .CAB file so you can start getting information how your clients actually are configured!
So take the time to create a baseline with everything that is important in your environment!!
What’s new in Configuration Manager 1708 Technical Preview
Today Technical Preview 1708 was released! Great new stuff as always. The Configuration Manager team release 15 releases of Configuration Manager in a year, 3 Current branch releases and 12 Technical Preview releases! That is simply amazing!! The Configuration Manager product team is doing an amazing job and the products capabilities goes beyond my wildest dreams!
How would have thought we would be where we are today when SMS 2003 was released??
What is new in the Configuration Manager technical preview?
Software Center customization’s using Client Settings including Company Logo!
No requirement for an Intune Subscription any more to modify the Company logo and colors in Software Center! Great Stuff!
It is also possible to configure which of the tabs in Software Center that should be shown, this is great. There is some confusion today about what the compliance tab in Software Center actually shows compliance for, so there is a use case right there!

The logo file must fulfill the following size rules to work.

As displayed here the Compliance Tab is no longer visible in Software Center

Reboot a computer using Client Notification!
Right-click tools are slowly being replaced by built-in features in the Configuration Manager console, this time around the possibility to reboot a client using Client Notification. Note that the command to reboot is only visible when you select a single computer and for collections only after you select Show Members in the Collections so that the collection is added devices node as “sticky” node.

If a user is logged on the Reboot settings for the client are honored and the reboot dialog is displayed.

Run Script on devices or a collection of devices with the possibility to pass optional parameters to the script.
The Run Script feature is truly a great addition making it possible to create and run Powershell scripts in the console on devices and collections of devices. I am sure we will see more and more improvements in this feature in the future. This time the possibility to use Optional parameters to the scripts are added.
Management Insight
I have nothing showing up in my Management Insight but I guess that more insight will be shared on this new feature when the official docs are live!
“Gain valuable insights into the current state of your environment based on analysis of data in the site database.”

I am sure there are more hidden gems in this release, I will update this post if and when I find them!
SCCM remote control and the ”Access this computer from the network” setting
When chasing high-privileged accounts as they are a risk, this is a question I have seen many times. In the Security Compliance templates from Microsoft (even the latest for RS2) the setting “Access this computer from the network” is recommended to be set to “Administrators” and “Remote Desktop Users” which is a good recommendation!
It however also stops SCCM Remote Control to work if you aren’t a member of the Local Administrators or the Remote Desktop Users group, as you are not allowed to connect to the computer even if you are a member of the Permitted Viewers group. Which is not so great as we don’t want those high-privileged accounts to be used to remote control the computer at all and specially in some scenarios. An example would be if a user needs application support, there is no purpose for the person remote controlling the session to be a member of the local administrators group as it is not needed to support the user.
The connection will never complete when the user is not member of a group that is allowed to access the computer from the network as shown below.

The solution is to simply add the SCCM Remote Control group you use to grant permissions to “Access this computer from the network” or add the SCCM remote control group to the Remote Desktop Users group but that would grant them more permissions as well.


Then remote control connection will now be successful even if they are not members of the local administrators group on the client.
Launching a task Sequence using an Application link in ConfigMgr 1706
With the new feature in Configuration Manager 1706 that makes it possible to launch Software center and show the correct application from a direct link in Software Center which is great! We can copy the link and email it to the user for instance.

I have a customer that wanted to send out a mail with a link for the users to start they upgrade to Windows 10 (Yes, with clear instructions before that this will happen so they know it is not a virus.)
We can only use the direct link to launch software center and show applications not packages or Task Sequences which is what I wanted to do.It will look like this example for the user, launched from Explorer.

Here is how I did it should be just fine doing it with PS App Deployment Toolkit as well.
I created a new application with the with the following files, I took the “Runsilent” utility from the “Web Service for OS Deployment” that my colleague Johan Schrewelius wrote which basically suppresses all dialog’s from Powershell for instance. It can be found here: https://gallery.technet.microsoft.com/Web-Service-for-OS-93b6ecb8

There are a couple of things to keep in mind.
- To launch the Task Sequence the application must be run with “Install as user” This will make it possible to use with PS App deployment toolkit as well and interact with the user for example.
- To make it succeed and not fail, I added a registry key to it which is written to current user in the registry that it is successfully launched.
Wrote a little Powershell script to launch a Task Sequence, I am sure I found the function on some blog a while back but cannot find it now 
The script I used, just change the name to match the Task Sequence you want to run. I will create a registry key called CCMEXEC\TSHasrun which we can use as detection method. The script can be downloaded here: Callts.ps1

We then add that script to the same folder as Runsilent.exe to make it run silent and add it to the runsilent.ini file.


In the application we use “Runsilent.exe” as a command line and “Install as User” as displayed below.


Then I deploy the application to a collection as a available so they can launch it from the link whenever they like.
I hope this is useful to someone and I am sure it can be improved and used to do other things as well.
Event forwarding and writing it to a SQL Database
I wrote a blog post over at 4Sysops.com about how to use event forwarding to capture events from clients and then write it to SQL. I have been using this for years now and there are so many ways this can be used, Applocker – Which apps are blocked, Windows 10 projects – how do we know that our computers are healthy and so on. The use of this is endless!
It is old technology but great stuff! Check out the whole post here: https://4sysops.com/archives/windows-event-forwarding-to-a-sql-database/
I will post some simple reporting services reports later this week as well.
Test application installers in System context using a Schedule Task
When deploying an Application using SCCM or Intune for that matter, the installation is run in System Context if you don’t select to run it as the user. I have answered this question I think once a day this week on Technet forum where the application fails when deployed using SCCM but works when tested manually.
To test an application that are to be deployed using SCCM/Intune it must be tested by installing it in System context not as a logged-on administrator, then you will spot all errors with custom actions in and MSI that checks for currently logged on user or issues like that.
To test an application Psexec, from SysInternals, is a great tool, there is however a simpler way, using the Task Scheduler which is already there. Psexec is not allowed by some Anti-Malware for instance but the Task Scheduler is.
I start by copying my installation files to C:\Temp on my test machine. Then launch Task Scheduler and select “Create a Task”
- Give it a name and set that it should run in System Context as shown below.
![]()
- Then we skip to the Actions tab and select “New”
![]()
- We use the “Start a program” task
And as an argument we use the following commands to run the .MSI silent and with verbose logging. /i “C:\temp\7z1701-x64.msi” /QN /L*V “C:\temp\7z1701-x64.log”
![]()
- Select OK

Then we ready to start our task to install 7-zip under the System Context by simply select “Run” in the Task we created.

When the task is finished 7-zip is installed, if we look in the verbose .MSI log file which was created during the installation, we can see that it was run under the System Context.

Really simple!
If we use Psexec we can use the following command after downloading and unpack psexec from here: https://docs.microsoft.com/en-us/sysinternals/downloads/psexec
Example command line for using psexec to test a Windows installer package in System Context:

The result is the same as using a Schedule Task.
Testing your applications in the correct context before deploying them will save you a lot of time and headache.
Happy testing!
What’s new in Configuration Manager Technical Preview 1709
After Ignite where Co-Management was announced, where we can manage a Windows 10 client both using SCCM on premise and using Intune and AzureAD, we can now test out this feature in Configuration Manager 1709 Technical Preview! While Co-Management is the biggest new feature in 1709TP, the VPN Profile creation wizard has gotten a whole new look to it as well.
Co-Management of a Windows 10 device with AD/Configuration Manager and AzureAD/Intune is a huge step towards the transition to Modern Management. With the modern threats and fast moving changes as Office 365, Windows 10, Onedrive for Business and all the As-A-Service solutions, managing these solutions the traditional way can for many organizations be really tough. Modern management could be an answer to at least some organizations and for the rest that has some really heavy legacy of applications, at least some users/devices can managed the modern way. And with Co-Management we can take the best of both worlds and use them as we transition to modern management.
Enabling Co-Management
To enable Co-Management we need the following pre-reqs inplace:
- Technical Preview for Configuration Manager version 1709
- Azure AD
- EMS or Intune license for all users
- Intune Subscription setup as standalone (Intune is the MDM authority)
- Windows 10, version 1709 (Fall Creators Update) and later
- Hybrid Azure AD joined (joined to AD and Azure AD
For more information check out the documentation: https://docs.microsoft.com/en-us/sccm/core/get-started/capabilities-in-technical-preview-1709#co-management-for-windows-10-devices
To enable Co-Management we go to the Administration tab in the console, select Cloud Services and there it is the new Co-Management tab.

From there we can select Configure Co-management and signing in to the Intune Subscription that should be used.

We select Pilot as we want to test it out, before we move all our clients.



My next test will be to move my newly installed Windows 10 Insider preview machines to the Pilot collection and test it out. This is going to be extremely useful to transition to modern management.
Updated VPN profile wizard
The updated VPN profile wizard now adopts the rest of the wizard after the platform you choose. For example if I choose Windows 10, only the options applicable for Windows 10 VPN profiles are presented to me.

If I choose Android, only the options applicable for Android is displayed

If we compare that to how the wizard looks like in Configuration Manager 1703 it is much easier to use in the new version.

Management Insight is also listed in the scenarios for new features, probably because it had some challenges in the previous Technical Preview.
Management Insight gives you suggestions on unused things in Configuration Manager, like Empty Collections and Applications without deployments. In larger environments with a great number of Applications and Collections it can be hard to find those unused things that are still in the console.

Powershell script to collect sccm log files from clients using Run Script
During my session at Techdays Sweden I demoed the new Run Script feature both in Configuration Manager 1706 and the enhancements made in the Technical preview after and showed how a variable can be used.
In the first demo I used the below Powershell script sample that will collect all SCCM Client log files in a Zip archive and copy them to a file share in a folder with the name of the computer the log files are from.
This could be one scenario to use with the new Run Script feature. The scripts are run almost instantly on the clients, one thing to note is that if the client isn’t online it has 1 hour to come online and run it otherwise it will not run.
Example one without parameters in Configuration Manager 1706:

When the script is run which we can track under script status.

And we have a new file in a new folder with the log files from the client.

If we do the same in the Technical Preview that supports variables we can remove the hard coded share name and use a variable instead.

We can then add a default value for the parameter in this case the logshare to be used.

And when we run the script we can change the sharename for where the log files should be copied.

The new parameter feature is great! Someone asked for the script I used and here it is.
$Logshare = "\\cmtp4\logs"
#Get path for SCCM client Log files
$Logpath = Get-ItemProperty -path HKLM:\Software\Microsoft\CCM\Logging\@Global
$Log = $logpath.LogDirectory
#Create folders
New-Item -Path $env:temp\SCCMLogs -ItemType Directory -Force
Copy-item -path $log\* -destination $env:temp\Sccmlogs -Force
#Create a .zip archive with sccm logs
Compress-Archive -Path $env:temp\Sccmlogs\* -CompressionLevel Optimal -DestinationPath $env:temp\sccmlogs
#Copy zipped logfile to servershare
$Computerlogshare=$logshare + “\” + $env:Computername
Write-host $Computerlogshare
New-Item -Path $Computerlogshare -ItemType Directory -Force
Copy-Item $env:temp\sccmlogs.zip -Destination $Computerlogshare -force
#Cleanup temporary files/folders
Remove-Item $env:temp\SCCMlogs -Recurse
Remove-item $env:temp\SCCMlogs.zip
In the Technical preview release we can also use Parameters with our script so I changed it so it asks for the $Logshare variable when executed in the console as shown below.
The only thing that is modified in the script to the version using variables is this line:
$logshare = "\\Server1\Logs\"
Which is replaced by
Param(
[string]$Logshare
) #end param
News in Configuration Manager 1710 Technical Preview
Technical preview 1710 of Configuration Manager is packed with new great improvements. Every time a new Technical Preview is released it is always a great time playing around with the new features that are available and testing them out.
This time around there are many great new features long asked for like support for 512×512 resolution icons in Software Center. Windows Defender Application Guard, Windows Defender Exploit Guard and Application control are great new additions in managing Windows 10 1709.
Let’s look at the news.
Run Script is a feature which is still being developed and improved and has great potential, in this release there are many news. When creating a script with a parameter we can no specify rules for the values supplied in the parameter and passed to the script as shown below. Security scopes can also be assigned to scripts in the console.

When running the script, we also have a new experience when supplying the parameter.

When the script is run the new way to monitor the result of the script is amazing. There are three different tabs in the result view. All shown below with different chart options, it looks great!!



Windows Defender Application Guard, Exploit Guard and Application Control
A great proof that the next release of Configuration Manager is the one that will support Windows 10 1709 to the full extent with the ability to configure the new features introduced in Windows 10 1709. Windows as a service starts with servicing of Configuration Manager.

Limited support for CNG certificates
Great news for everyone using HTTPS or planning to, support for is coming for Cryptography API: Next Generation (CNG) certificate templates for the following scenarios:
- Client registration and communication with an HTTPS management point.
- Software distribution and application deployment with an HTTPS distribution point.
- Operating system deployment.
- Client messaging SDK (with latest update) and ISV Proxy.
- Cloud Management Gateway configuration.
Support for up to 512×512 icons in Software Center
Software center can now display icons with a pixel dimensions of up to 512×512. Pretty counts!!
![]()
Limit Windows 10 Enhanced telemetry
It is now possible to Limit Windows 10 Enhanced telemetry to only send data relevant to Windows Analytics Device Health. This is a great new option which hopefully will make more customers use the new Device Health feature which gives great insight in drivers that causes errors and more.

Device Guard policy improvements
My favorite new Device Guard Policy is this one in the 1710 TP release, “Automatically run software trusted by the Intelligent Security Graph” This is great feature that can increase security with a minimal administrative overhead. You can read more about the Intelligent Security Graph here https://www.microsoft.com/en-us/security/intelligence
More content has been Branchcache enabled like script, Phil over at 2Pint has a really good post about it here: https://2pintsoftware.com/branchcache-mp-configmgr/
Now I will test out all the new features including Co-Management!
Creating a dynamic Azure AD Group for Corporate owned devices
One of the most common requests I get when deploying Intune is that they want to deploy for instance a Certificate, VPN, WiFi or a specific app only to corporate owned devices and not personal(BYOD) devices. We have Dynamic groups in AzureAD that can solve this for us, however when I looked at the documentation on Microsoft docs it was not correct. So here we go:
To create a Dynamic Azure AD group for Corporate owned devices here is how we can do it:
- We create a Dynamic Device group
- Add a simple rule shown below that uses deviceOwnership and includes all devices marked as Corporate, If want one for Personal devices we can create a new one and change it to Personal instead.

We can also create a Dynamic Group for all Corporate Owned iOS devices. Instead of using a Simple rule we create and Advanced rule as shown below.

Then we can deploy the Certificate, VPN app or whatever we want to a these groups instead.
Dynamic groups are awesome!
Configuration Manager 1711 Technical Preview is now released..
..and it was shipped by the MVP’s attending the Configuration Manager MVP Summit 2017! It was me and Kim Oppalfens(@TheWMIguy) who got to ship it as a reward for our competition on Twitter the last year on who’s is the fastest to test the new features in each Technical Preview! A great honor!

As we all wait for the release of Configuration Manager 1710 release there is not that many features in the new Technical Preview release, guess the team has been busy with the CB release. However a long awaited feature is on that list and that is the possibility to allow users to interact with an application deployed to System and set to run “Whether or not a user is logged in or not”. A question I got on Twitter when tweeting the picture is if the application can be added to a Task Sequence when that setting is used and the answer is YES.

There are some really neat Compliance settings as well which is new in this release as well. For example it is possible to set required Windows 10 Builds for MDM managed Windows 10 devices.

Nested Task Sequences also got some more love in this release, the limitations that was in the previous Technical Previews now seems to be resolved. Be sure to test it out!
Now the testing continues!
Installing applications and packages dynamically during OSD
I wrote a post way back where I used a Powershell script to query AD group description for Applications to install dynamically during OS deployment in Configuration Manager. There was a couple of comments and recently a request to extend that script to also install packages dynamically during OS Deployment. The old post can be read here: http://ccmexec.com/2016/05/installing-applications-dynamically-during-os-using-ad-group/
So here it is as promised, this script will install both applications and packages/programs during OS deployment dynamically.
It will read the description of AD groups and match it using a Prefix and Suffix to identify groups used for Applications / Packages. In the Description field for AD groups used for applications we add the application name and for packages we the packageID and program to run like shown below.

To use it:
- Save the script below and edit the following lines so it matches the environment it is run in
$Prefix = “A.”
$Suffix = “.i”
$SiteCode = “060” - Create a package with the script so we can run it in a Task Sequence
- Add the script to the Task Sequence using the run Powershell script command
![]()
- Add an Install Application Step using these settings.
![]()
With the following condition so it is skipped if the are no applications to install
![]()
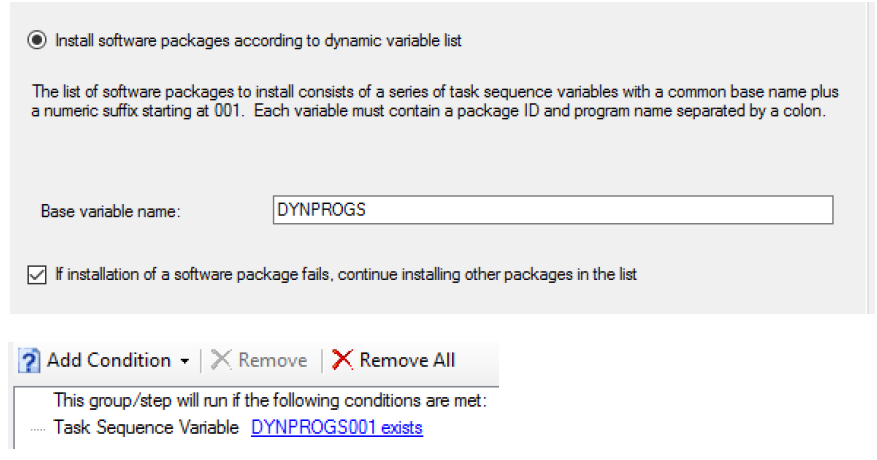
- Add an Install Packages Step using these settings.
![]()
With the following condition so it is skipped if there are no packages to install
![]()
The script:
# Written by Johan Schrewelius / Jörgen Nilsson
# http://ccmexec.com
# Version 1.1
# Added fallback to _SMSTSMAchineName if OSDComputerName is missing
# Thanks to Daniel Marklund for testing and adding features (Nested groups)!
# Version 1.2
# Update 2/12/2017: Added support for PackageID:Program in description attribute – Limitation: Application name must not start with SiteCode
$Prefix = “A.”
$Suffix = “.i”
$SiteCode = “060”
$tsenv = New-Object -COMObject Microsoft.SMS.TSEnvironment
$CmpName = $tsenv.Value(“OSDComputerName”)
if(!$CmpName) { $CmpName = $tsenv.Value(“_SMSTSMachineName”) }
$ADObjectDN = ([ADSISEARCHER]”samaccountname=$($CmpName)`$”).Findone().Properties.distinguishedname
$AllGroups =([ADSISEARCHER]”member:1.2.840.113556.1.4.1941:=$ADObjectDN”).FindAll()
$DescList = $AllGroups.Path `
| Where { ($_ -replace ‘^LDAP://CN=([^,]+).+$’,’$1′).StartsWith($Prefix) -and ($_ -replace ‘^LDAP://CN=([^,]+).+$’,’$1′).EndsWith($Suffix) } `
| Foreach { ([ADSI]”$_”).Description }
$AppCount = 1
$PkgCount = 1
$DescList | Where { !$_.StartsWith($SiteCode) } | Foreach { $tsenv.Value(“COALESCEDAPPS” + ($AppCount++).ToString(“00”)) = “$_” }
$DescList | Where { $_.StartsWith($SiteCode) } | Foreach { $tsenv.Value(“PACKAGES” + ($PkgCount++).ToString(“000”)) = “$_” }
That is it.
What’s new in Configuration Manager 1712 Technical preview AKA “MVP Edition”
Back in November during the Configuration Manager MVP Summit 2017 we did a hackathon that week which was amazing fun! Some of the features that was being worked on during that week is now in the Configuration Manager 2712 Technical Preview that was just released. The official documentation is here: https://docs.microsoft.com/en-us/sccm/core/get-started/capabilities-in-technical-preview-1712
There are some really great features in here like Client PXE, Last Logged on user in device view and Multiselect of Application in Software Center. I hope more of the things we talked about and worked on that week will make it in the next Technical preview as there was some really cool stuff!
No Let’s have a look at these new cool features.
Client-based PXE
Wow!! This is mindblowing, that is something I never thought would ship with Configuration Manager ever. Ronni Pedersen wrote a great blog post in how to make a client in the 1711 Technical Preview with the DP role to act as a PXE server https://www.ronnipedersen.com/2017/11/19/sccm-enable-desktop-clients-as-pxe-servers/ . The Distribution Point role should not be needed anymore in this release.
When testing it I didn’t get it to work, I can see it responds just fine but it is missing a file ☹ I will update this when I get it to work.
How it works, we need to distribute the Boot image to the client cache on the computer. I did that with a Task Sequence that simply downloaded the content.
Then we can enable clients to respond to PXE requests which can be done using a Custom Client Setting.

When configured this we go the client and after the policy is downloaded a new log file shows up the C:\Windows\CCM\Logs folder SMSPXE.log
And in there we can see that it actually responds just fine.

Do not automatically upgrade superseded applications
This was also part of the Hackathon I was a part. Finally!!!! Supersedence is fixed!!!!  Based upon your user voice feedback, in this release you have the option to configure an application deployment to not automatically upgrade any superseded version. Now when creating the deployment, on the Deployment Settings page of the Deploy Software Wizard, for either Available or Required install purpose, you can enable or disable the option to Automatically upgrade any superseded versions of this application.
Based upon your user voice feedback, in this release you have the option to configure an application deployment to not automatically upgrade any superseded version. Now when creating the deployment, on the Deployment Settings page of the Deploy Software Wizard, for either Available or Required install purpose, you can enable or disable the option to Automatically upgrade any superseded versions of this application.
Device list displays primary user
There are two new features in the Device view in the console.
Primary users column are now visible per default. And “Last Logged on User” is a new Optional column that can be added. Extremely useful!


Improvements to Office 365 client management dashboard
The Office 365 client management dashboard now displays a list of relevant devices when graph sections are selected.
Install multiple applications in Software Center
This is a great new feature, I was in the Hackathon group that worked on this. We can no install multiple applications using multi-select in Software Center. Will save much time in many scenarios.

Renamed collections display in existing collection membership rules
This solves a very annoying behavior when working with collections. So now when a collection is a member of another collection and it is renamed, the new name is updated under membership rules
Allow user interaction when installing applications as system
Was introduced in the 1711 Technical preview but still listed as a new feature in Technical Preview 1712. This gives us the possibility to allow users to interact with an application deployed to System and set to run “Whether or not a user is logged in or not”. A question I got on Twitter when tweeting the picture is if the application can be added to a Task Sequence when that setting is used and the answer is YES.

Surface Devices Dashboard
The Surface dashboard now displays firmware version for Surface devices rather than operating system version.

And as always it is now time to continue testing and see if there are more features hidden in this release!
Troubleshoot boot issues and drivers by enabling Boot log during OSD
Troubleshooting driver issues when the computer stops during OSD when booting with the infamous circle showing or nothing at all showing is a big challenge. With all the modern 2-in-1 devices and devices using USB-C docking stations I have seen this a couple of times the last month.

One option that at least gives us an idea of which driver it is that actually causes this is to enable Boot logging, which has been around a while now. Boot logging can be manually activated using MSconfig as shown below. It can also be enabled using command line “bcdedit.exe /set {current} bootlog Yes”

It gives us a log file, C:\Windows\ntbtlog.txt with all the drivers loaded during boot. It will also log drivers that failed to load, so if it freezes or stops the boot process we can at least see what driver it loaded as the last one. The log file is not overwritten it will append to the log file.

Enabling it during OS deployment is really simple, just a command line to enable it directly after the Setup Windows and Configuration Manager step and then we add reboot for it to take effect.

It is not perfect but can be helpful when troubleshooting boot/reboot issues during OS deployment.
Manage SCCM configuration items and baselines with community tools – 4Sysops
I wrote a post on a couple of tools to manage Configuration Items and Baselines in Configuration Manager over at 4SysOps. I covered four tools in that blog post.
- Registry to PowerShell converter (Reg2CI) by Roger Zander
- PowerShell Policy Editor by Roger Zander
- Configuration Manager Remote Compliance by Trevor Jones
- Create ConfigMgr Configuration Items from Group Policy Object by Sam Robert
A big thanks to Roger Zander @roger_zander, Trevor Jones @trevor_smsagent and Sam Robert for creating and sharing these awesome tools!!
Read the whole post here: https://4sysops.com/archives/manage-sccm-configuration-items-and-baselines-with-community-tools/
Phased deployment in Configuration Manager 1801 Technical Preview
Configuration Manager 1801 Technical preview contains some really cool features. The biggest one is defiantly the Phased Deployment option that we see the first version of. It basically adds a new deployment option to Task Sequences (I just assume it will be for applications in the future as well) called Phased deployment. It is similar to the Automatic Client Upgrade, you set a Pilot Collection and a Production Collection.
In the phased deployment option we can set what success rate a deployment must reach before it is automatically approved to the Production collection. The docs talk about an option to do this manually but I cannot see it in the Technical Pilot for now at least. Let’s hope a lot of more options will arrive to this great new feature.
We can also set Stop criteria if the deployment reaches an threshold of failed deployments.
Many use scripted solutions or manual solutions to solve the same scenario. I recorded an animated .Gif with the options we have today so you can see how it looks in the Technical Preview.
And as always provide feedback on what more options you want to see for this new feature!! Looking forward to see this in the next CB release (I hope!!)
SCCM Dynamic Driver management using Onevinn SCCM Extensions
My co-worker Johan Schrewelius has written a cool extension to Configuration Manager that adds some great features. In this post I will cover how it can dynamically manage drivers and driver software as we often must install that as well to get everything working. The end goal is to be able to add hardware models to our environment without having to modify our Task Sequence. Onevinn SCCM Extension can be downloaded here: https://gallery.technet.microsoft.com/SCCM-Extensions-for-driver-be30b298 and contains a pretty good documentation that will get you started. I will only cover the functionality in this article.
The parts of the Onevinn SCCM Extensions that are used to achieve this is:
Onevinn WebService, which is used to query the SCCM server for driverpackage/package to be used and software/applications related to a Hardware model.
SCCM Extension, which adds a new node on the Operating Systems pane in admin console and saves the HW model, drivers, Operating System, Software installations in WMI on the Site Server.

Using this addon we can configure a specific Hardware model which operating system used, and for that Operating System, select Driverpackage or a Package which many of us use today instead of a driver package(it will list all Package which starts with “DRV-“ in the name as Driver Packages).
if the hardware model has been inventoried in SCCM so it exists in the Database already it will be listed in the drop-down menu, if not in the DB already it can be added using the “New” button.
We can also select which applications and/or packages that should be installed in the Task Sequence during OS deployment.
In the Task Sequence we need to add three steps, that is all it takes.
Install Driver package(It requires that a package have been created with the .exe file and a configuration file, it is all covered in the documentation that is included in the download on Technet gallery), must be added after “Apply Operating System Image” and before the “Setup Windows and Configuration Manager” step, exactly where we run the Apply Driver Package step today.

That step will query the webservice for which driver package to use and then download it and apply it for the specific model and Operating System Image being used. It will look like this on the client during OS deployment where the drivers are downloaded and installed Dynamically

Install Software Dynamically
The DriverInstallerClient.exe also sets a variable for all Dynamic Software that needs to be installed so we only need to add the below step for the software to be installed dynamically during OS deployment.
Install Applications Dynamically
The DriverInstallerClient also sets a variable for all Dynamic Applications that needs to be installed so we only need to add the below step for the applications to be installed dynamically during OS deployment
The result is a much shorter Task Sequence than we have had before and it is dynamic, we can add a hardware model without editing the Task Sequence! 
I hope you find it useful as well, test it out, provide any feedback you have then we can make it even better in the future!!
Run server side code and commands in a safe way during SCCM OSD
This is part 2 of my posts about Onevinn SCCM Extensions that my colleague Johan Schrewelius has written and posted on TechNet Gallery: https://gallery.technet.microsoft.com/SCCM-Extensions-for-driver-be30b298
It includes Modern driver management features but also an extension to execute Server Side commands during OS deployment in the Task Sequence to replace Scripts and Webservices.

This functionality is a direct response to the fact that the world is turning rougher. We can no longer expose this kind of functionality trough a web service, which in practice is a low security interface to Configuration Manager and/or Active directory. Instead we have implemented a windows service that monitors Configuration managers own status message que and picks up requests made from the clients during deployment. It is, of course, highly recommended to switch to HTTPS haven’t you already.
All “sensitive” commands that were available in the previous release of the Onevinn web service have been replaced with a predefined TS command, just choose from the drop-down list:
The “Note” box will provide basic help regarding necessary argument:

In the event the built-in commands are not enough it’s possible to run custom scripts!! 

In this case a script called “TEMPLATE_AD.ps1” is run with parameters -OSDComputerName and -ResourceID.
Any script in the “C:\TSScripts” folder can be invoked the same way.
The service account used for TS Commander will, depending on which functionality is invoked, need matching permissions in AD and SCCM.
Again test it out, provide feedback so it can be improved if you miss something.